Security Strategy
Firewalls or Phishing? Policies or People? If you don't know where to start your security journey, Willsley Consulting can help you develop a security strategy tailored to the needs and capabilities of your organisation.

The challenge
What do security and orchestral music have in common?
...Neither exist by themselves. Orchesteral music comes from all the instruments in an orchestra being played in harmony, keeping to time and reinforcing each other. In the same way, security comes from your people, processes, and technology being secured and supporting each other.
Just as the challenge for a composer is selecting the right instruments for their vision, you need to select the tools and methods to keep your organisation secure. However, what will secure a five person organisation won't help a 500 person one, conversely, the security setup for a 500 person organisation will likely be too onorous and/or expensive for a five person one.
The solution
Security Strategy based on openly accessible standards
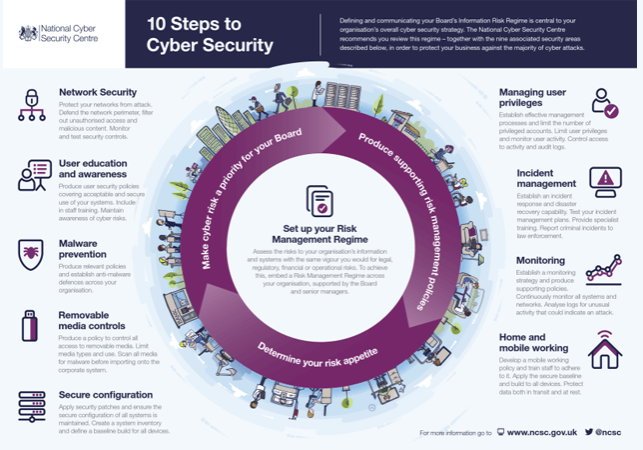
We base our Security Strategy engagements on the 10 Steps to Cyber Security which is published on behalf of the UK Government by the National Cyber Security Centre (NCSC) and is a free to use set of resources backed by comprehensive documentation that helps small to medium organisations implement effective security.
Our strategy engagements also consider the requirements of the international standard for information security - ISO/IEC 27001.

The results
Understand your security priorities, with flexible accreditation
Following a Security Strategy enagement, you will understand what good security looks like for your organisation, and where it sits relative to that. You'll also have a plan for addressing any shortcomings that is tailored to your organisation, budget and timescales.
Furthermore, it is possible to gain accreditation for your organisation's security by way of a Cyber Essentials or Cyber Essentials Plus award, along with accreditation against ISO/IEC 27001. Achieving these can be integrated into our strategic planning and can help turn security into a selling point for your organisation.
What's involved in a Security Strategy engagement?
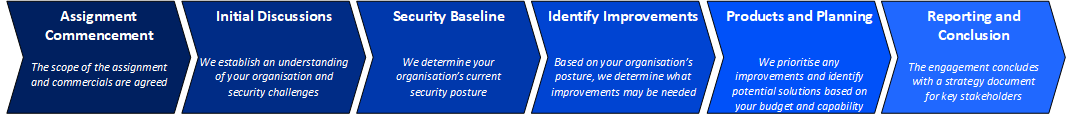
Because no two organisations are the same, no two engagements will be either. A Security Strategy engagement will generally consist of the following steps:
Learn More
Email support@willsley.com or complete our online contact form to get a call back to discuss your organisation's needs.
How we use your information
If you use the contact form, the information you enter will be emailed to support@willsley.com. Google ReCaptcha is used for spam prevention and may set cookies on your system to enable this functionality. Disabling cookies may therefore prevent use of the form.
By using our form, or emailing us regarding a Security Strategy consulting engagement, you're consenting to receive emails and/or phone calls relating to this service. Regardless of how you contact us however, we will never sell your information.
While persistence may pay off, we appreciate it's frustrating to keep receiving unwanted emails and calls. As such, we'll contact you once in relation to your query, and again to follow up if we haven't heard back from you. If we still can't reach you, or you haven't replied after this, we'll remove you from our contact list.
If you want us to remove you from our contact list at any other time, please email us at support@willsley.com and we will remove you from our contact list.